The Campus Watch Crime Prevention Manual
Campus
Watch is the community based crime prevention program and organization for the
faculty, staff and students of
Campus
Watch is organized under the auspices of the Rice University Police Department.
The Rice Police Department was recognized in 1996 for having the most
outstanding crime prevention programs in the state of
WHAT IS CAMPUS WATCH?
In a
nutshell Campus Watch is the people of
Each member is required to attend a one hour intensive training session on crime prevention theory and practical application. This session is augmented with a training manual that will allow the volunteer to educate him or herself on the topics not covered in the session.
Once trained, the volunteer is invited to assist the crime prevention officer in conducting a security survey of their office and classroom area.
Monthly meetings are held for the entire membership. Crime prevention information on pertinent topics are presented at each meeting by either a member of the University Police or a guest speaker.
Each Campus Watch member is a link in the Emergency Phone Network. When a violent crime has been committed, the Campus Police initiate a call to a Watch Captain. He or she will in turn notify the other Watch Captains in his or her college and the Watch Members on the Captains floor or area. Within about thirty minutes all available volunteers have the facts rather than the rumors that inevitably spread when a violent crime occurs.
THE GOALS OF CAMPUS WATCH ARE:
To provide a forum for the exchange and coordination of ideas, concepts, and strategies to prevent or reduce crime.
To educate members of the
To focus attention on issues relating to crime prevention.
To encourage extensive citizen and community involvement in the reduction of crime and criminal opportunity.
To share with all segments of the campus community and the CAMPUS WATCH organization, matters relating to the continued development of a comprehensive plan for the prevention of crime at Rice.
To
encourage the education of all members of the
To encourage maximum cooperation and communication between all segments of the Rice University community in addition to improving communications between all community members and the Rice University Police toward the goal of crime prevention.
TO LEARN
MORE ABOUT CAMPUS WATCH OR TO BECOME A VOLUNTEER AT
FOR MORE INFORMATION:
crod@ruf.rice.edu and am@ruf.rice.edu
CAMPUS WATCH MANUAL
RISK MANAGEMENT: Liabilities and Safety on Campus
CRIME PREVENTION AND SAFETY
SUSPICIOUS PERSONS
Campus
Watch is a community based crime prevention organization. It is designed for
the faculty, staff and students of
The
Campus
Watch is organized under the
Campus Watch has two major objectives. The first objective is to prevent criminal activity or to reduce its frequency. The second objective is to increase the protection for the individual members, their colleagues, and property. These objectives are accomplished through education. This takes place through monthly meetings, guest speakers and special training seminars.
Campus
Watch is the citizens of
Campus Watchers network through the Emergency Phone Network. This is a pyramid that allows information to be distributed throughout the community in a rapid fashion. Further networking is accomplished through the Phone/Fax/E-mail network.
Campus
Watch is the cooperation and communication between the
THE ROLE OF THE CAMPUS WATCHER
As a Campus Watcher, you have become a vital link between your college and the Rice Police. Many people complain among themselves about criminal activity. They never do anything about it. They never report it to the police. Because of your personal commitment to the Campus Watch program, you are no longer one of these people. You will now become a person who does something about it.
GETTING INVOLVED
The first
step in becoming a Campus Watcher is training. In this training you will learn
the theories of crime prevention. You will learn how to best protect yourself
while on campus. You will learn to assess the physical risk in your work and
living area. Vehicle crime is a chronic problem in large cities, and
How a victim is chosen. Then strategies will be given to assist you in protecting yourself, both on campus and in your daily life.
Your responsibility will be to take this knowledge back to your college, to your floor or wing, to your family and to your friends. Practice these strategies for crime prevention regularly and urge others to do so. These techniques are designed to reduce your chances of criminal victimization.
Another responsibility will be to report suspicious persons and activities to the Campus Police. By doing this you assist the police in working to prevent crime, establish patterns of activity, and identify suspects. Police Officers on the daily assignments will stop in from time to time.
Every college experiences a certain amount of turnover. You should provide safety information to your new students.
Campus
Watch is the people of the
Crime prevention can be defined in many different ways. It is the anticipation, recognition and appraisal of a crime risk, and then initiating some type of action to reduce or remove it. This process can also be termed risk management.
The Four D’s
To help us remember the premise of Risk Management, we need to remember: detect, deny, deter, and delay.
1. DETECT: An assessment must be made of a particular area. This assessment establishes whether the area is a crime risk. Contributing factors would include: criminal history, structural security, and personal liabilities. When all these factors have been established and assessed, a crime risk has been detected. Primary areas of hardware to inspect are lights, locks, and alarms.
2. DENY: Since we have detected a crime risk, we now must do things to either eliminate or reduce it. We want to deny the criminal the opportunity to commit the crime. The best option is to deny any opportunity to let a crime be committed. Sometimes this is not possible. We are bound by rules and regulations; we are effected by financial constraints. We must use prudent judgment on when to make changes to deny risk. Denying risks may call for upgrading a structure, changing a behavior, or requiring an individual to be somewhat inconvenienced.
3. DETER: Making the crime risk absolutely impregnable is not always possible. That is okay. Just because you cannot establish total invulnerability does not mean that an effort should not be made to reduce a detected crime risk. If we cannot make the area crime proof, let us make it so difficult for the criminal that the risk of getting caught, is not worth the fruits of the crime. Upgrading hardware is always an option. Lighting can always be upgraded, but it is just as important to make sure that the existing fixtures are fully operational. If it is too expensive, the existing hardware can be repaired so that it works as best as it can. Lighting can always be upgraded, but it is just as important to make sure that the existing fixtures are fully operational.
4. DELAY: The best example to use for delay, is an automobile theft. If a thief wants to steal your car, there is nothing that you can do to prevent it. Every alarm system can be defeated given time. With the crime risk that we have detected, we want to delay the criminal. Criminals want to get in and get out fast. By making them stay longer, there is a greater chance that they will be detected. We need to implement items in our crime risk that slow a criminal down so much that
The biggest crime that happens on the Rice campus every year is the “opportunity theft”. This is a very preventable crime. All it takes is personal responsibility.
image008.jpg" v:shapes="_x0000_i1029">
To
illustrate opportunity theft, we will refer to the triangle. A triangle is a
three sided geometric figure. If you should remove any side of the triangle,
the structure collapses. The same is true of opportunity theft. It has three
sides. Side one we will label as Desire. There must be desire on the part of an
individual to commit a crime. Side two we will label as Skills. The perpetrator
must possess certain abilities to commit the offense. In opportunity theft, the
skills need be great. How difficult is it for a thief to pick up a coat, put it
on and walk away? How difficult is it to pick up a backpack and walk off
undetected with it.
You are expected to set an example for stopping opportunity theft, but you are to educate others in your college about opportunity and the precautions they must take to avoid them. Reminders, both verbal and written will be helpful to those who occasionally forget.
Be aware of your area. Know who is in the area to assist you. Know who belongs, and who does not belong.
Know how
to use your campus phone. Remember that the number for the Rice Police is
713-348-6000 or campus ext. 6000. If you are off campus, dial
Use the Escort Service when you are working late at night.
Know the location of the nearest Emergency Phone in the area you are in.
Remember that a suspect looks for one person alone.
University property, and personal property is stolen from offices at an alarming rate. Many times this is because we become complacent. Be aware! Be attentive. Never showcase your office, your property, or the university's property.
Close and lock your office when it is not occupied.
Encourage your coworkers to lock their offices.
Lock your desk, file cabinets, locker, etc.
Put your valuables away at night.
Consider having office hardware secured.
Have a representative of the Rice Police Department conduct a security assessment of your office.
ALWAYS LOCK YOUR CAR
CONSIDER INSTALLING AN ALARM
INSTALL AN “IGNITION OR GAS PUMP CUTOFF”
USE A STEERING WHEEL LOCKING DEVICE
Thefts from vehicles are also a problem. This takes place when an individual uses their car as an auxiliary locker, office, or storage facility. Property left in plain sight is an invitation to a thief to steal. The window gets broken out. The property gets removed, and the thief is quickly gone. The solutions are simple.
Do not leave anything of value in plain sight in your vehicle.
Place property in the trunk.
If you have a hatchback or a similar type vehicle place all property nearest the back, then cover it with an old blanket.
Always roll up your windows and lock you car when you leave it.
Bicycle theft is an ongoing problem. If you haven't already, you should record the make, model and serial number of your bicycle and store the information in a safe place. It is also a good idea to register your bicycle with the police. The Campus Police provide this service free. Online bicycle registration, R.I.D.E.; RegisterIDentify Educate, is available at http://rupd.rice.edu/bicycle/ .
While it is not possible to make your bicycle 100% theft proof, there are some simple steps you can take to increase the security of your bicycle and its parts:
Use a casehardened “U” lock; cable locks are easily cut
Lock your bicycles in racks provide by Rice University
Remember to also lock parts attached with quick release mechanisms
Below are some pictures of bicycles. Some are locked more securely than others.
|
|
1. Poorly Locked This bike's owner has a good lock, but is using it incorrectly. The lock is fastened to the cable loop on the rack and not the rack itself. The cable is the most easily defeated part of any bike security system. The u-lock should be through the frame of the bicycle and secured to the rack, with the cables looped through the wheels and then onto the u-lock. |
|
|
2. Poorly Locked This bike has quick-release mechanisms on the wheels, so the cable should be looped through the wheels to prevent them from being stolen. If possible, this cable-type lock should be avoided. |
|
|
3. Not Locked This bike's owner has taken the time to loop the rack cables through the bike wheels and has secured the rack latch. The only thing missing is a lock. No matter how little value you place on your bicycle, there's someone who will steal it. Even a $5.00 lock is better than no lock at all. |
|
|
4. Securely Locked This bicycle is locked securely. Notice that the u-lock is locked to the bike frame and the rack post. Also notice that the rack cable is looped through the front wheel and attached to the u-lock. If the rear wheel also had the cable looped through it, this bike would be very secure. |
|
|
5. Securely Locked This bicycle is locked securely. Notice that the u-lock is locked to the bike frame and the rack post. Also notice that the rack cable is looped through the front wheel and attached to the u-lock. If the rear wheel also had the cable looped through it, this bike would be very secure. |
|
|
6. Very Securely Locked This bicycle is locked very securely. Notice that the u-lock is locked to the bike frame and the rack post. Also notice that the rack cable is looped through both the front and back wheels and attached to the u-lock.
|
BURGLARY AND THEFT PREVENTION
Operation Identification is a citizen burglary/theft prevention program used in home and businesses. The Operation ID program involves the marking of property with an identifying number as a means of discouraging burglary and theft. In communities where it has been properly implemented, Operation Identification has shown dramatic results in its ability to reduce burglary and theft.
At Rice
the Operation ID program has two parts. First, engrave your valuables with your
Driver's License Number or your
The
SUSPICIOUS PERSONS
What is suspicious?
What makes someone suspicious?
How do you know if something “funny” took place?
The answer to all these questions is largely subjective. Sometimes an individual will look perfectly normal in one area of the campus, while this same individual’s presence would be highly irregular in another part of campus. The best way to articulate suspicion is: If something, or someone's presence makes you feel that all is not right, you need to articulate this information to the police.
If something out of the ordinary takes place in your office/classroom or college, you need to articulate it so that the dispatcher knows what has taken place. You know your office/classroom or college better than anyone. If something is not right, then you need to articulate it. An example: Every day you lock your desk, file cabinet, and turn off the computer, then, on a Monday, you discover the office open, the computer on and your desk rummaged through; this is suspicious. If you work in an isolated area where students never, or rarely, frequent and a person who looks like a student is just hanging around for a long time, this may be suspicious.
When you talk to the dispatcher, articulate these things. Somebody that is ‘very suspicious’ isn't going to report his or herself to the police.
DESCRIBING A SUSPICIOUS PERSON
How do you describe a suspicious person?
The first thing to do is plan now how to do it, so that the description is of use to a police officer looking for them. Do not be shy; do not think your description might be offensive.
After you have tried to articulate these identifiers, go one step further. Ask yourself, if I were going to draw a caricature of this person, what features would draw your attention? Stress and articulate the obvious.
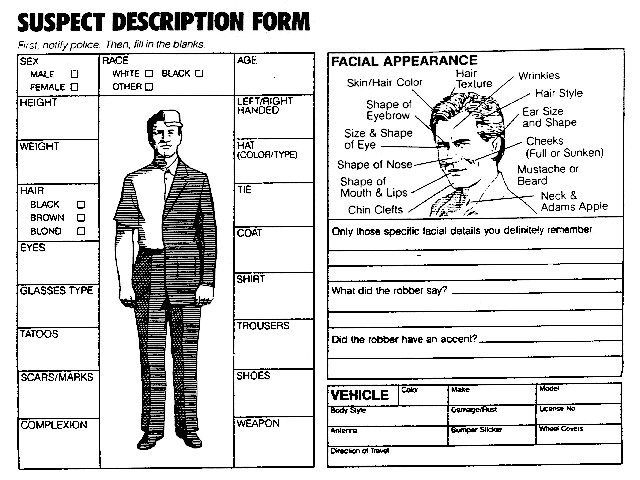
Suspects SEX
Suspects RACE
Did the suspect have a weapon?

Revolver

Semi-Automatic pistol

Shotgun

Assault Rifle
If the suspect was in a vehicle, what type and color?
|
4 door |
Coupe (Compact) |
2 door Sports Car |
Van |
SUV |
Truck |
Remember! The most important part of a vehicle is its License Plate.
Get the State and Plate Number if possible.
CAMPUS WATCH EMERGENCY PHONE NETWORK
PURPOSE: To advise the Campus watch community of the occurrence of an event, or description of a suspect.
In turn, all Campus Watchers are expected to relay the information to all faculty, staff and students in their office, in their immediate area, on their floor, on in their building.
The Phone Network provides accurate information and all the available information. This information helps eliminate gossip, rumors, and inaccuracies. The Phone Network relays the correct information as quickly as possible. Within fifteen to thirty minutes, the entire Campus Watch membership should be notified of the who, what where, when and how the event occurred.
USAGE: The Phone Network will be used for certain crimes (i.e. robbery, assault, rape) where serious or heinous acts have been committed. The Network will also be used for lesser crimes (misdemeanors) where there is a named suspect or great description.
HOW IT WORKS: Information relating to any event is given by the victim to the police officer and the police dispatcher. A member of the Rice Police Department will initiate the network by calling each College Officer. The College Officer will then contact the floor Captains in a method approved by the College Watch. Each floor Captain is responsible for contacting all the members in his or her area and usually one other area Captain.
APPENDIX A
The Block or Watch Captain is the primary link in the Campus Watch chain of command. The duties of a Captain include a wide range of simple tasks.
Meet each resident in your assigned area and explain to them what the Campus watch is about. Enlist their support.
Maintain an emergency phone list of all your assigned residents.
Be available to pass on information about criminal activities in your area. (Notice: You may be called late at night.)
Forward
information to the
The Captain also coordinates assistance programs if there are any special needs in their area and may set up social events for their members to be involved in.
The most important part of a watch is the members. Being a watch member is not a hard or time consuming job. It mostly involves becoming aware of activities in your area and taking time to report them.
Observe
and report any suspicious activities to the
Report the non emergency activities to your Captain on a 3X5 card or telephone him or her.
Report an emergency to the Police immediately
After you contact the police inform your Captain
Be willing to serve as an acting Captain in the absence of your area Captain and to assist the Captain with projects in your area.
Attend monthly/quarterly meetings of your watch group
--------------------------------------------------------------------------------